
In late August, Quentin Dempster outlined the scale of information the government will legally force ISPs to collect.
The list is extensive to say the least:
For emails
• Who you’ve emailed
• Date, time you sent email
• Attachment data volumes
For Phone
• Phone number of everyone you called
• Missed numbers
• 1800 numbers
• Number of everyone you SMS’d
• Time, date of calls and SMSs
• Duration of calls
• Your rough location at time of call or SMS
Online activity and social media
• Your IP address
• Time and duration of your web connections
• The law does not require carriers to retain ‘destination’ IP addresses (your web browsing history), but a carrier may do so
• The volume of your uploads and downloads
• Location and geographical data
The list of agencies authorised to access this information without a warrant is extensive, and is not exhaustive:
• ASIO (Australian Security Intelligence Organisation)
• Australian Federal Police
• All state and territory police forces
• The Australian Commission for Law Enforcement Integrity
• Australian Crime Commission
• Australian Customs and Border Protection Service
• Australian Securities and Investments Commission
• Australian Competition and Consumer Commission
• NSW Crime Commission
• NSW Independent Commission Against Corruption
• NSW Police Integrity Commission
• Queensland Crime and Corruption Commission
• West Australian Corruption and Crime Commission
• South Australian Independent Commission Against Corruption
• Any other agency the Attorney General publicly declares
Law enforcement and Intelligence agencies will have immediate, warrantless and accumulating access to all information required to be retained by law, and ISPs and telcos that choose to disagree can be penalised for $2 million for non-compliance.
Baker & McKenzie’s Fair told Fairfax Media a person’s metadata can be reviewed at any time by agencies without that person’s knowledge and it might be used for or against you in court.
“The issue here is not so much the weaknesses in the Privacy Act but the lack of real time supervision and accountability of law enforcement and national security agencies. Our supervisory regime is weak and unlikely to ensure proper use of the extensive data soon to be kept,” Fair said.
Another issue is the safety of this stored information
At a CeBIT technology conference in Sydney this year, cyber security expert Kevin Mitnick said the laws appealed to illegal hackers.
“They are extremely attractive because of the information that is stored,” he said.
“In my experience everything is hackable, so you hope the government agency or the third party provider has very high security standards,” he added.
Metadata requests are not new.
In 2013-2014, there were more than 330,000 requests for access to metadata on Australians.
A spokesperson for the Attorney General’s Department said metadata was a vital tool used in “virtually every counter-terrorism, organised crime, counter-espionage, cyber-security, child exploitation and serious crime investigation”.
Greens Senator Scott Ludlam put it quite succinctly.
“This is a bill to entrench a system of passive mass surveillance. It is corrosive of the very freedoms that governments are elected to protect, and it has no place in a democracy. And yet, it is a democratically elected parliament that [has enacted it].”
It gets worse.
The Telecommunications Interception Act requires all communications providers to have a real time interception capability.
The Australian government has gone from the protector of the people to the Ministry of Love.
What we are seeing now is a move away from isolated cases of identifying criminal activities, to the dragnetting of an entire nation in the hope that within millions the criminals are also caught. Thomas Drake, a former NSA agency analyst, at a Walkley Foundation seminar in Sydney said that the NSA’s enormous data surveillance project had not exposed or halted any terror plots.
Regardless of whether or not this assists in the interception of terror plots, there is no doubt that it is a huge invasion of the right to privacy every citizen has come to expect.
To react accordingly, something must be done to ensure the right to privacy is retained.
Enter the VPN
A VPN (or Virtual Private Network) is a method used to add security and privacy to private and public networks.
When using a VPN and you visit a website, you send a request to another computer. That computer sends out your request and returns the information. This means, your connection is hidden behind another connection. No-one can see what you’re doing online because you’re hidden behind a different computer with a different connection. This can traverse through multiple connections creating a virtually impossible to trace network.
This is your connection without a VPN:
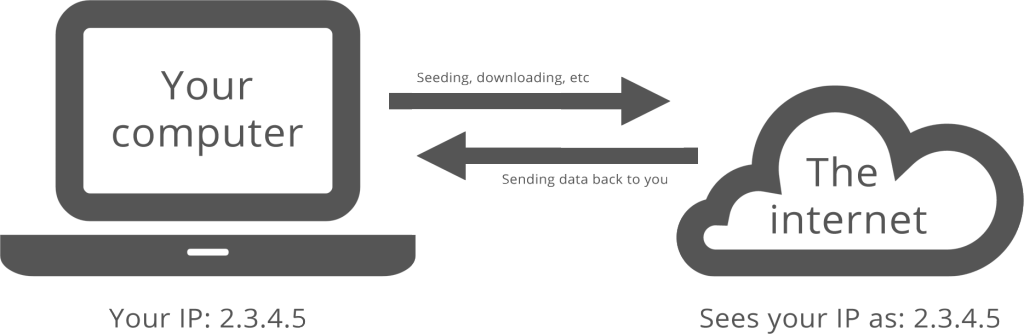
This is very clear-cut. And the Australian government will be able to collect everything outlined above during this type of online communication.
When using a VPN, the conversation looks like this:
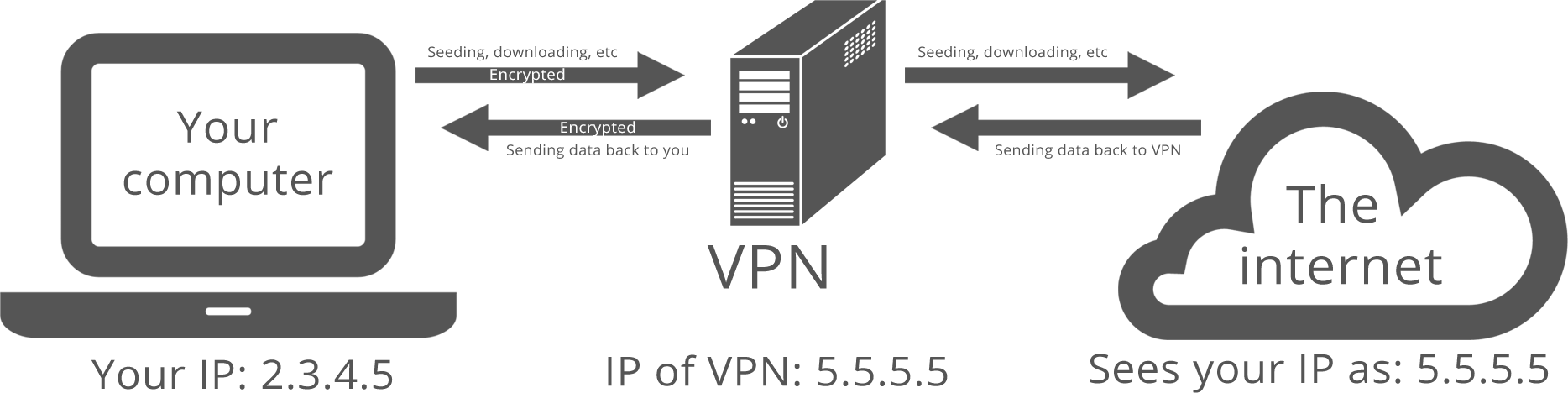
The benefits of opting for a VPN here are glaringly obvious.
Using a VPN
One option for a safe VPN is Cryptostorm.
What sets them apart from the rest of the herd is the team behind the product and their extensive knowledge in the field.
The have been aware of the imminent changes to data retention in Australia and have responded accordingly.
The Cryptostorm.is ‘Sexy Narwhal’ Widget
Had nothing to do with VPNs before? The process of getting started is not as convoluted as it once was.
In fact, using Cryptostorm as an example, getting started is a simple matter of acquiring a token, downloading the software and clicking Connect.
That’s it.
Now all traffic and browsing flows through one of many locations around the world and metadata is safely filtered from the prying eyes of the Australian government.
For more information and other services, check out Torrentfreak’s 2015 list of VPN services that take anonymity seriously.
Pair a VPN with the TOR Browser and your online activity is virtually anonymous, safe and difficult to track.
You can learn more through the Data Retention Protection Guide on the Pirate Party Australia website.

